Well, in the past article, we studied what is pBFT, and its advantages and disadvantages in detail. But you must be curious about its working or functioning. Now in this guide, let’s look at the working of pBFT. So, without wasting any time, get into the topic.
Listen to the full article on audio
How does pBFT work?
pBFT attempts to provide a sensible solution that can function even when suspicious and harmful nodes are present and are operating in the device.
Nodes in a pBFT enabled distributed system are ordered or designed subsequent to each other such that one node is the primary(like its leading) and others are mentioned as secondary(or the backup nodes). The point that needs to be noted here is that any eligible secondary node in the system can make the transition from secondary to primary to become the primary node. This happens mostly in the case of a primary node failure. The aim is that all nodes assist to reach a consensus concerning the state of the system using the majority rule.
The condition for a Practical Byzantine Fault Tolerant system to work is that the maximum number of malicious nodes must not be greater than or equal to one-third of all the nodes in the system. The system becomes more secure with an increasing number of nodes.
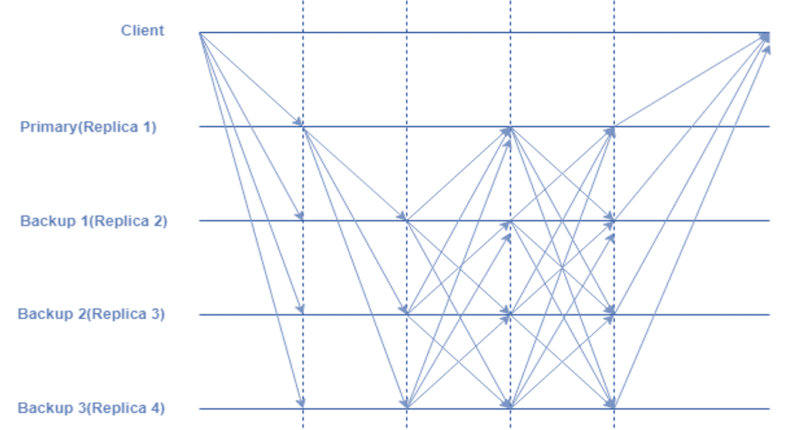
pBFT consensus rounds are divided into 4 phases:
- The client makes a request to the primary(leader) node.
- The primary(leader) node makes broadcasts of the client’s request to all the secondary(backup) nodes in the network.
- The nodes including both the primary and secondary perform the service requested and then send back a reply to the client.
- If the client receives ‘m+1’ replies from different nodes in the network with the same result, then the request is considered to be served successfully. where the ‘m’ represents the maximum number of faulty nodes allowed.
During every view(pBFT consensus rounds), the primary(leader) node is changed and can be substituted by a view change protocol if a predefined quantity of time has passed without the leading node broadcasting a request to the backups(secondary). If required, a maximum of the honest nodes can vote on the legitimacy of the current primary node and substitute it with the next leading node in line.
Platforms using pBFT variants:
- Zilliqa – pBFT in combination with PoW consensus
- Hyperledger Fabric – permissioned version of pBFT
- Tendermint – pBFT + DPoS(Delegated Proof-of-Stake)





-260x140.png)